Table of Contents:
- What are Data Privacy and Data Security?
- Why Are Data Privacy and Data Security Important?
- Types Of Data Security
- Data Privacy and Data Security
- Best Practices for Data Privacy
- Best Practices for Data Security
Let’s take a closer look at Data Privacy and Data Security to understand how different organizations can manage information and foster trust.
You’ve probably heard the phrase “Data is the new oil,” and it’s true that data is now propelling a growing number of organizations. Accessing data has become extremely easy in this digital world, which has created a thin line for our confidentiality. Companies are keen to gather information in order to provide personalized customer experiences, automated marketing notifications, and science-driven insights, all of which are reliant on the quality and volume of your data.
In the past 2 years, organizations have been under mounting pressure to adopt digital technologies and meet evolving customer expectations—a phenomenon that is expected to continue into the future.
Because data is an important factor in every decision, interaction, and process, successfully managing data to make sure Data Privacy is considered will be critical.
Data Privacy has been a constant concern. A single company may hold the personal data of millions of customers—information that must be kept encrypted in order to keep customers’ identities as secure and safe as possible, as well as ensure the company’s reputation remains untarnished.
However, Data Privacy is more than just a business concern. When it comes to Data Protection, you as an individual have a lot on the line. The more you understand about it, the better prepared you’ll be to protect yourself from a wide range of dangers. In this article, we will take a closer look at what are Data Privacy and Data Security and unpack why it is critical to an organization’s success.
What are Data Privacy and Data Security?
It can be challenging to keep up with concepts and regulations as new Data Privacy laws continue to emerge. Data Privacy refers to the responsible use and processing of an individual’s private information by restoring the individuals’ ownership of their data. Personal data protection ensures that data is kept confidential. This concept is where Data Privacy transitions to Data Security and Data Protection.
In general, Data Privacy refers to a person’s ability to regulate when, how, and to what extent personal details about them are shared with or communicated to others. This information may include a person’s name, location, contact details, or online and offline behavior patterns.
Many online users want to control or prevent certain types of data collection, just as they may wish to exclude people from a private conversation.
As Internet usage has grown over time, so has the value of Data Security. In order to offer services, websites, apps, and social media platforms frequently need to gather and store personal information about users.
Some apps and platforms, on the other hand, may not meet users’ expectations for data collection and usage, leaving users with less privacy than they actually realized. Others may not put adequate protection around the data they hold, leaving them open for a data breach that could seriously jeopardize user privacy.
Like Data Privacy, the phrase “Data Security” is somewhat vague and not necessarily intuitive. This confusion is particularly true when comparing Data Privacy and Data Security concepts. Data Security is the practice of preventing unauthorized access, corruption, or theft of digital information during its entire lifecycle.
It is a term that includes all aspects of Data Security, from storage and hardware devices, and physical security to administrative and access controls, in addition to the logical security of software platforms. It also contains guidelines and procedures for the organization.
When implemented properly, robust Data Security techniques help shield an organization’s data assets not only against cybersecurity attacks but also from insider threats and human error, which continue to be among the top reasons for data breaches today.
Information Security entails deploying technologies and tools that improve the organization’s visibility toward where and how their critical data is kept. Ideally, these tools should be able to apply security measures such as encryption, data masking, and sensitive file redaction, as well as automate reporting to simplify audits and make sure that regulatory requirements are met.
Why Are Data Privacy and Data Security Important?
When sensitive information gets compromised, things can go wrong. A data breach at a government agency, for instance, could put sensitive data in the hands of an adversary. A corporate breach can put proprietary data in the hands of rivals.
A school data breach could put students’ personal information in the hands of criminals who might use it to perpetrate identity theft. A breach at a hospital or doctor’s office can put private health information (PHI) in the hands of individuals who could misuse it.
Types Of Data Security
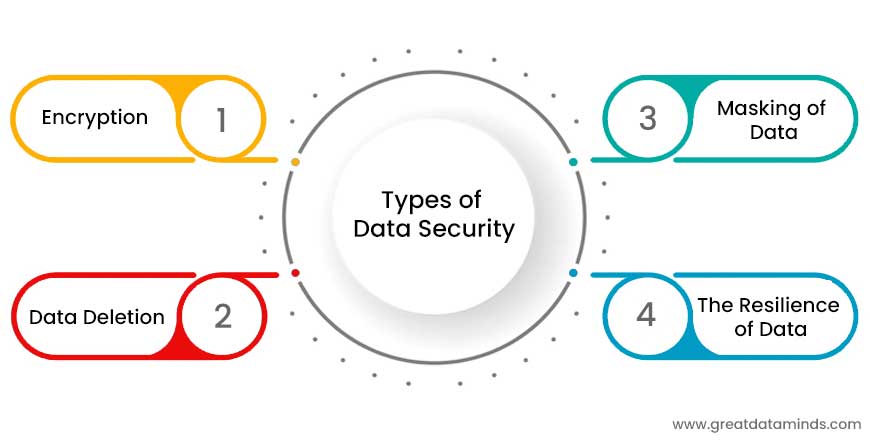
-
Encryption-
Encryption keys scramble data by employing an algorithm to convert normal text into an unreadable format that only authorized users can view. Document and database encryption solutions protect sensitive volumes by obscuring their contents through encryption or tokenization. The vast bulk of solutions also includes security key features.
-
Data Deletion-
Data deletion, which is far more secure than standardized data wiping, employs software to completely overwrite data on every storage device. It ensures that the data is not recoverable.
-
Masking of Data-
Organizations can permit teams to create apps or train employees using actual information by masking data. It masks personally identifiable information (PII) where needed so that development can occur in compliant environments.
-
The Resilience of Data-
The ability of an organization to withstand or recover from any kind of failure – from hardware issues to power failures and many other circumstances that impact the availability of data – determines its resilience (PDF, 256 KB). To minimize the impact, recovery time plays a critical part.
Data Privacy and Data Security
| Data Privacy | Data Security |
| Data Security is a necessity for Data Privacy. | Data Security is the primary requirement for Data Privacy. |
| Data Privacy governs the collection, retention, deletion, and storage of information. | Data Security establishes the policies, methodologies, and means for safeguarding personal information. |
| It allows you to prevent websites, web browsers, wireless carriers, and internet service providers from monitoring your information and browsing history. | It promises to safeguard you from unauthorized access to your private details as well as other data. |
| Data Privacy refers to reflecting on what and why data is important. | Data Security is all about representing how those regulations were implemented. |
| Browser extensions and add-ons, password managers, private browsers and email services, encrypted messaging, private search engines, web proxies, file encryption software, and ad and tracker blockers are examples of Data Privacy Software. | Identity and access management, data loss prevention, anti-malware, anti-virus, event management, and data masking software are all part of Data Security tools. |
| The General Data Protection Regulation (GDPR) of the European Union is a kind of international standard for safeguarding EU citizens’ privacy. | The Payment Card Industry Data Security Standard contains a set of guidelines for protecting sensitive credit and debit card information and cardholder data. |
Best Practices for Data Privacy:
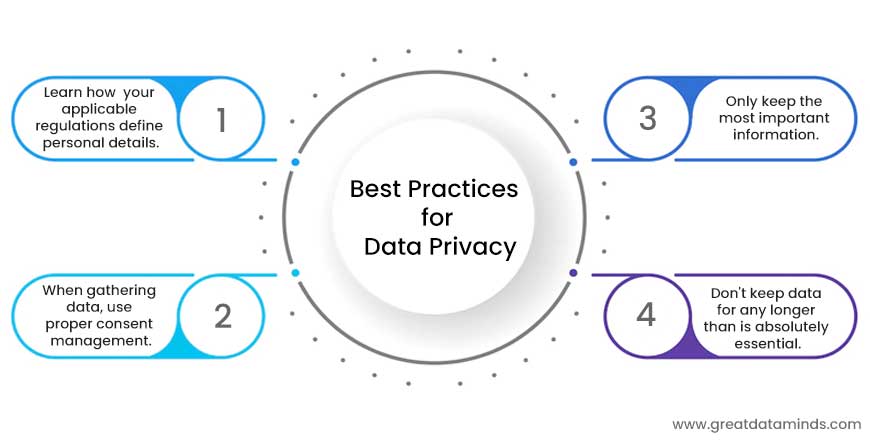
- Learn how your applicable regulations define personal details.
- When gathering data, use proper consent management.
- Only keep the most important information.
- Don’t keep data for any longer than is absolutely essential.
- Learn about individuals’ data rights under the relevant laws and regulations. Comply with such requests when individuals submit them, for example when they object to the sharing of their information.
Best Practices for Data Security:
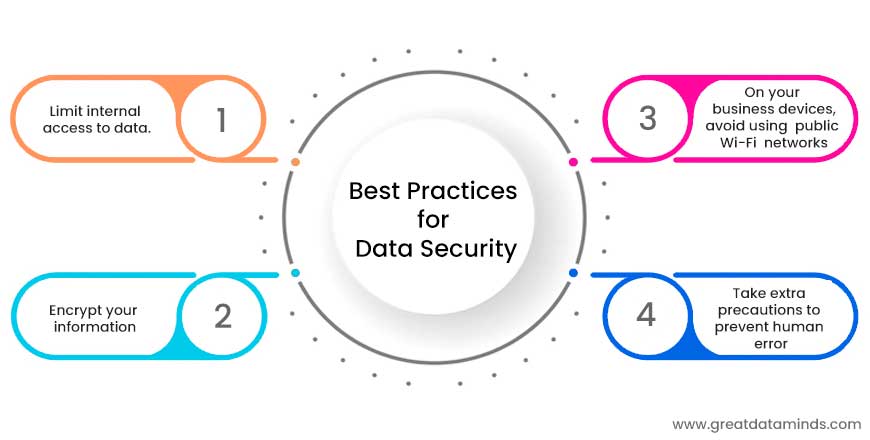
- Limit internal access to data.
- Encrypt your information.
- On your business devices, avoid using public Wi-Fi networks.
- Take extra precautions to prevent human error.
Final Words
The days of quietly collecting and distributing personal information are over. Organizations that store and use financial, health, and other sensitive information must now treat that data with care. Using best practices will help support your organization in developing a basic privacy framework that allows it to become a responsible and moral custodian of personal information. Data Protection, Data Privacy and Data Security are significant factors to understand. And, even though they are all intimately connected, they symbolize completely different approaches and concepts. Updating your data policies and staying up to date on best practices and guidelines can help keep you and your customers safe from cybercrime and data breaches.






